Code execution in Cisco Secure Client with NAM
17/05/2024 - Téléchargement
Product
Cisco Secure Client with NAM
Severity
Medium
Fixed Version(s)
5.1.62
Affected Version(s)
< 5.1.62
CVE Number
CVE-2024-20391
Authors
Description
Presentation
Secure Client harnesses the powerful industry-leading AnyConnect VPN/ZTNA and helps IT and security professionals manage dynamic and scalable endpoint security agents in a unified view.
Issue(s)
When Cisco Secure Client is using NAM (Network Access Manager) and Windows Wi-Fi contextual menus are replaced by those of Cisco, an attacker with physical access can execute commands as SYSTEM on the affected machine.
Timeline
| Date | Description |
|---|---|
| 2024.03.25 | Advisory sent to Cisco |
| 2024.03.25 | Case opened by Cisco |
| 2024.04.01 | Cisco confirms the bug |
| 2024.04.30 | Cisco states that release 5.1.62 fixes the vulnerability |
| 2024.05.15 | Cisco releases its advisory |
| 2024.05.17 | Public release |
Technical details
Code execution as SYSTEM
Description
When a laptop has the Cisco Secure Client installed with the NAM module and Windows Wi-Fi context menu is replaced by those of Cisco, then when accessing a locked laptop, a Cisco window can be opened from the logon screen.
![]()
When clicking this button, Cisco Secure Client context menu opens:

Then, a Wi-Fi network can be added:
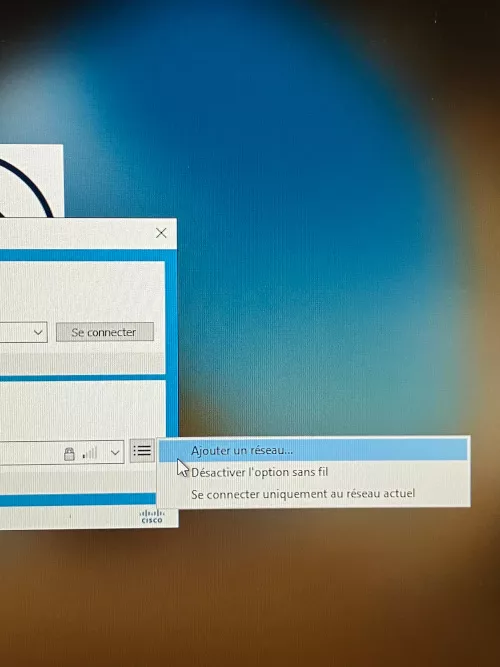
A menu with configuration options is opened:
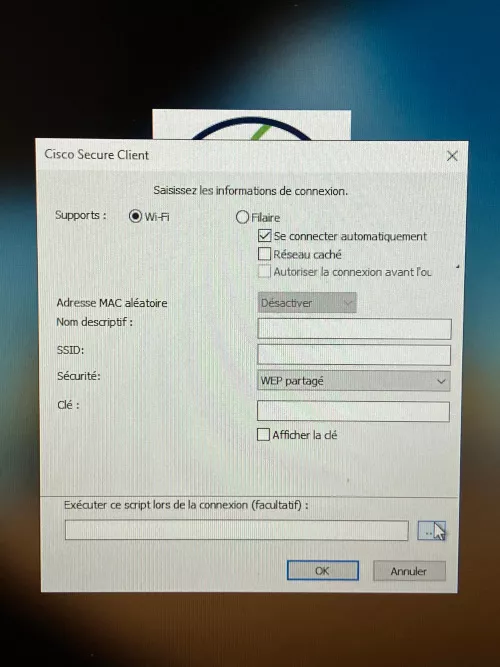
An option allows specifying a script to be executed when establishing the newly configured connection. The icon to choose this script opens an explorer:
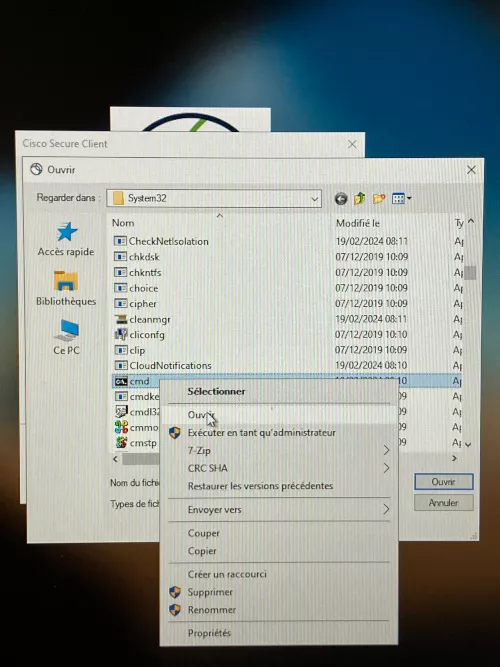
Upon choosing cmd.exe, a command prompt is run under the SYSTEM account.
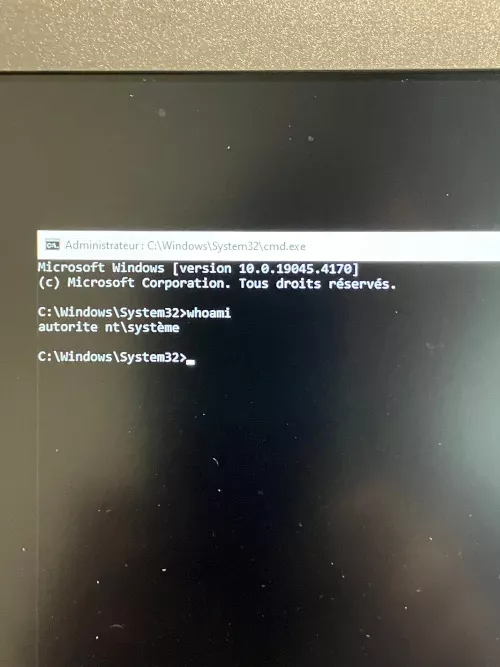
Impact
This behavior allows running any command under the NT Authority/System account which has the highest privileges. This allows compromising the underlying machine and accessing any data it contains.
