Livewire: remote command execution through unmarshaling
08/01/2026 - Téléchargement
Product
Livewire
Severity
Critical
Fixed Version(s)
>=3.6.4
Affected Version(s)
See section "Affected versions"
CVE Number
CVE-2025-54068
Authors
Description
Presentation
Livewire is a full-stack framework for Laravel that allows you to build dynamic UI components without leaving PHP.
Issue(s)
A pre-authenticated remote code execution vulnerability affecting Livewire 3 has been identified during June 2025.
A full blogpost detailing this vulnerability in depth can be found here: https://www.synacktiv.com/en/publications/livewire-remote-command-execution-through-unmarshaling.
Affected versions
Version 3.0.0-beta.1 to 3.6.3 are affected.
Timeline
| Date | Description |
|---|---|
| 2025.06.12 | Advisory sent to support@laravel-livewire.com |
| 2025.07.17 | Release of the version 3.6.4 containing the patch |
| 2025.07.17 |
CVE-2025-54068 assigned
|
| 2025.12.23 | Public release |
Technical details
Livewire: remote command execution through unmarshaling
Description
A pre-authenticated remote code execution vulnerability affects Livewire, it can be exploited by smuggling synthesizers through the updates field on any Livewire's request.
Impact
An attacker that identified a page updating a snapshot by calling /livewire/update for example, will be able to force a cast on an arbitrary Livewire component field.

In this example, the count field is updated as an array:
POST /livewire/update HTTP/1.1
Host: 192.168.122.184
Content-Length: 407
Cookie: XSRF-TOKEN=ey[...]%3D
{
"_token": "KAzJ4mhO8NzK8hMkAPjslaNo6hG2W740HoBDzSzA",
"components": [
{
"snapshot": "{"data":
{
"count":1
},
[...]
}",
"updates": {
"count": []
},
"calls": []
}
]
}
HTTP/1.1 200 OK
Host: 192.168.122.184
Set-Cookie: [...]joiIn0%3D; expires=Wed, 17 Dec 2025 18:44:31 GMT; Max-Age=7200; path=/; samesite=lax
{
"components": [
{
"snapshot": "{"data":{
"count":[
[],
{"s":"arr"}
]
},
[...]
}",
}
],
"assets": []
}
If this cast is successful, it is possible to trigger a remote command execution on the server as demonstrated on the following schema:
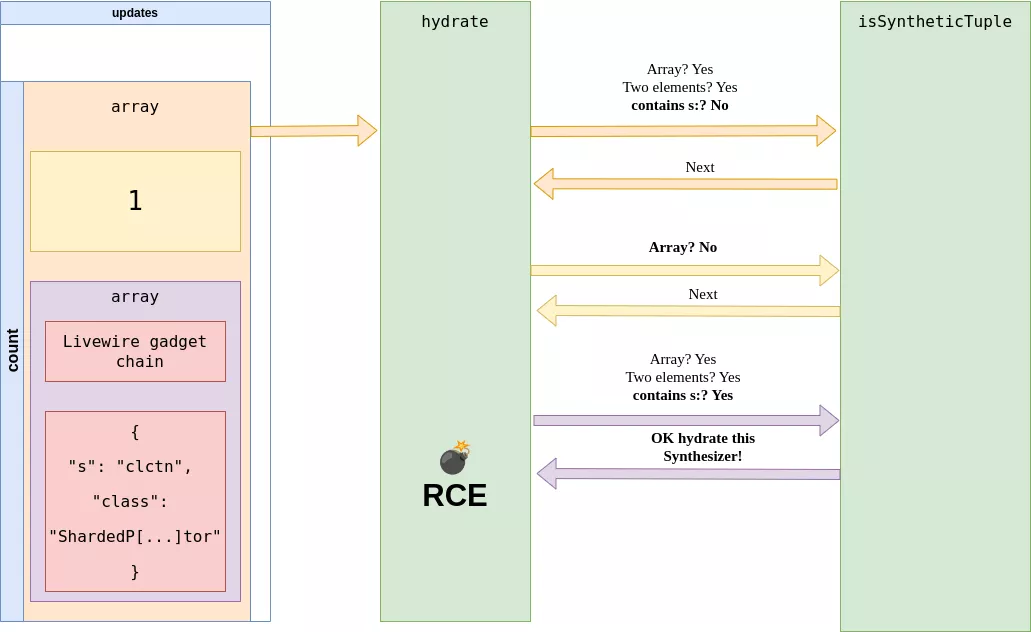
The tool Livepyre can be used to automate the exploit process of this vulnerability:
Recommendation
Upgrade Livewire to version 3.6.4 or greater.
Regenerate a new APP_KEY if you were exploited, the php artisan key:generate command can be used to do so. It is mandatory not to skip this step, an attacker in possession of the APP_KEY can still compromise the server.
IOC
Failed attempts to exploit the vulnerability will generate logs such as the following:
Cannot assign array to property App\Livewire\LivewireComponent::field of type ?string
/var/www/html/vendor/livewire/livewire/src/Mechanisms/HandleComponents/HandleComponents.php (442)
/var/www/html/vendor/livewire/livewire/src/Mechanisms/HandleComponents/HandleComponents.php (342)
/var/www/html/vendor/livewire/livewire/src/Mechanisms/HandleComponents/HandleComponents.php (318)
/var/www/html/vendor/livewire/livewire/src/Mechanisms/HandleComponents/HandleComponents.php (98)
[...]
However, a successful attempt might be totally logless if cast attempts were successful.
