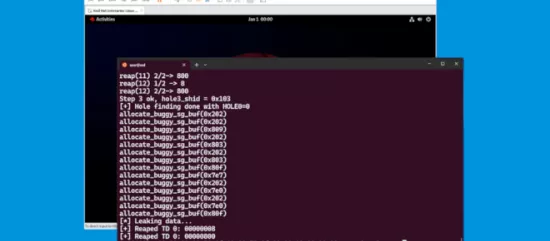
Cybersecurity is now the crux of the matter
Political and industrial espionage
Ransom demand via ransomware
Reputational damage
Destruction of information assets
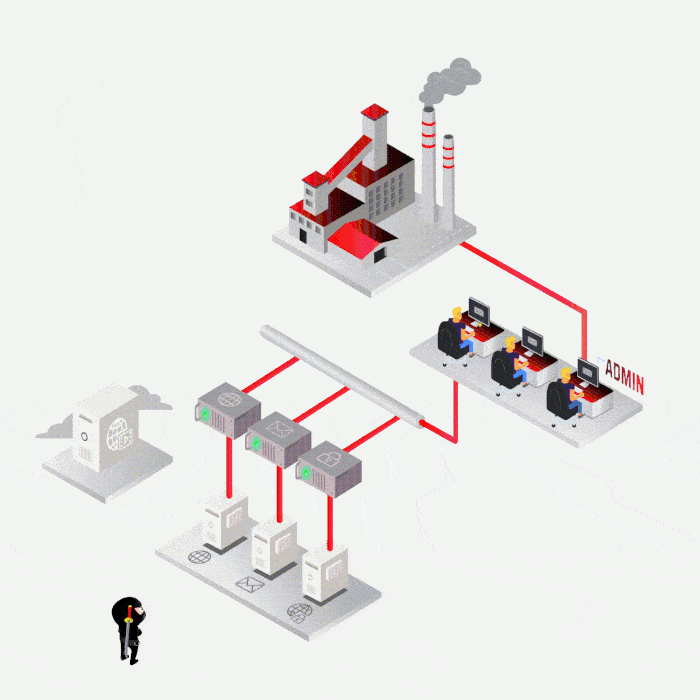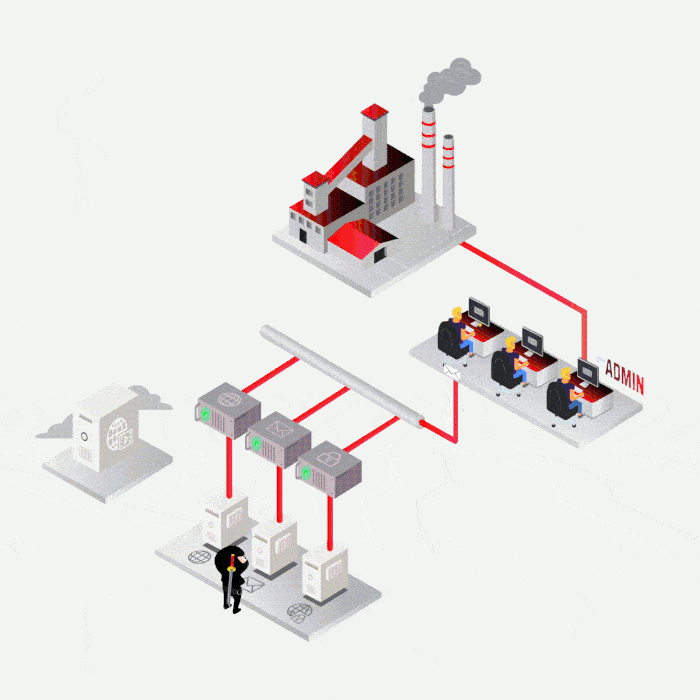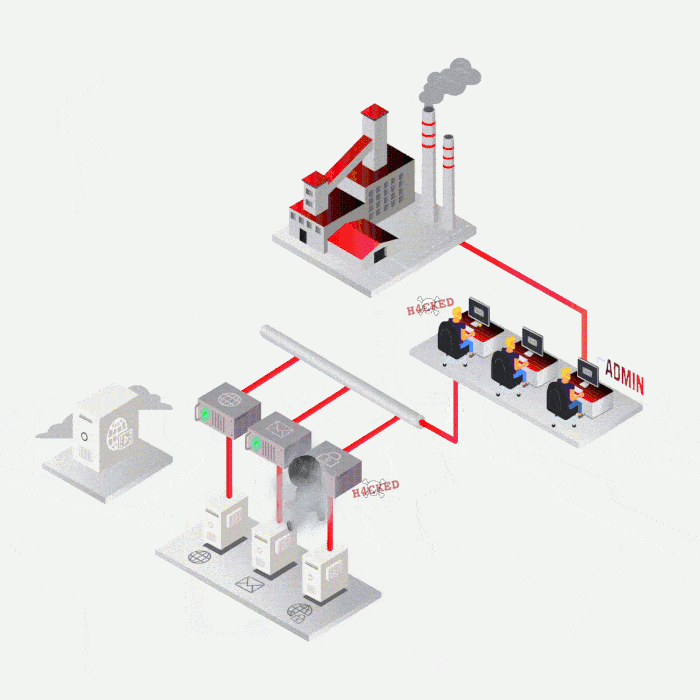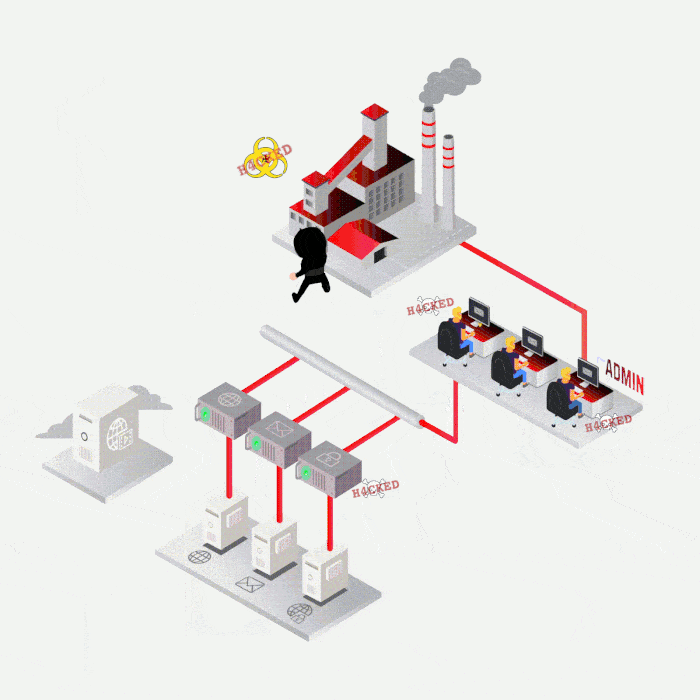
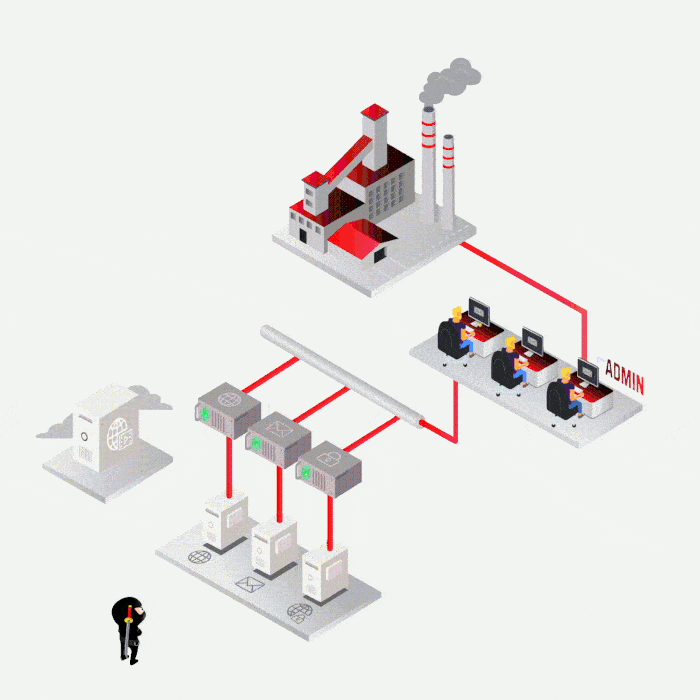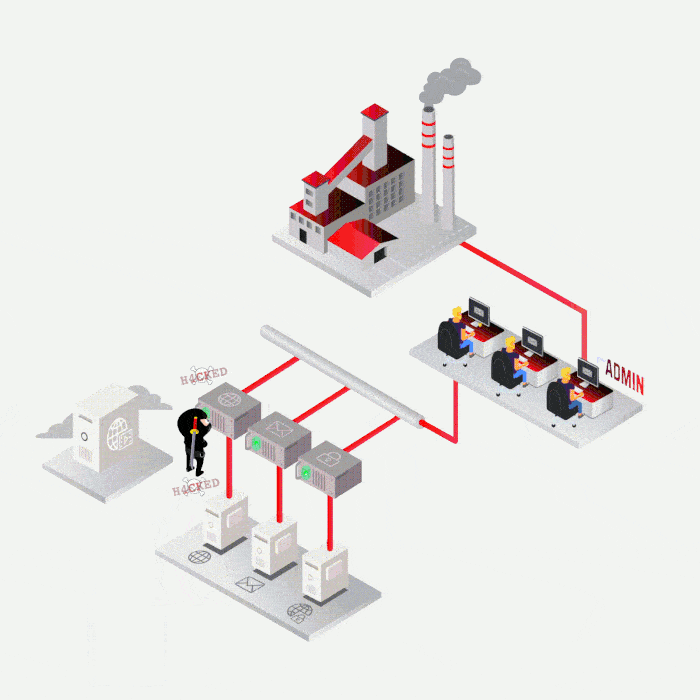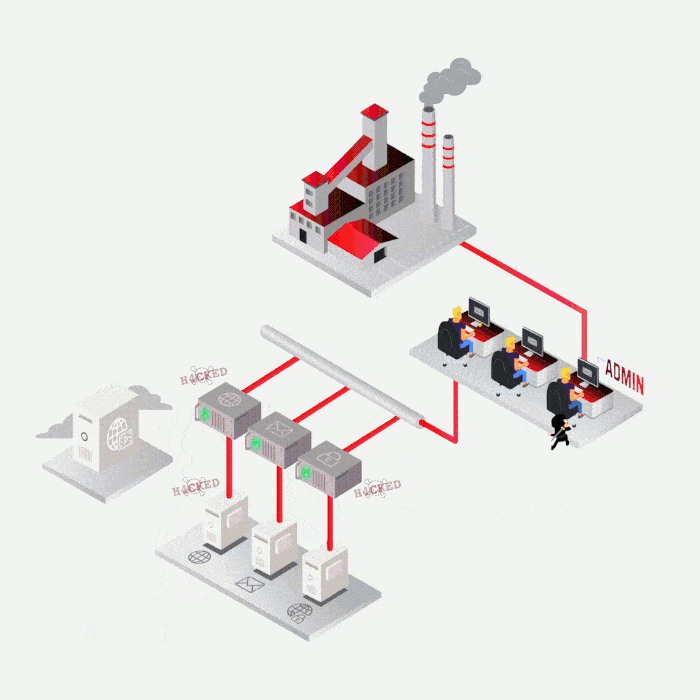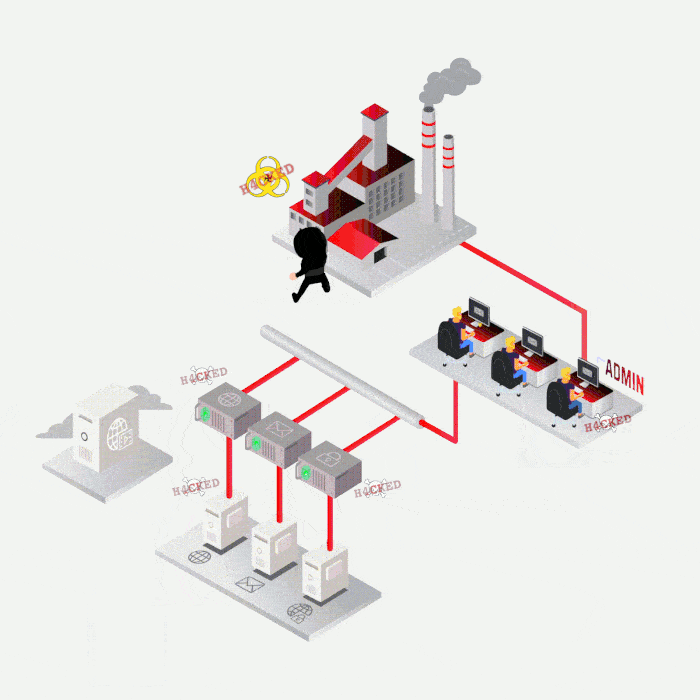
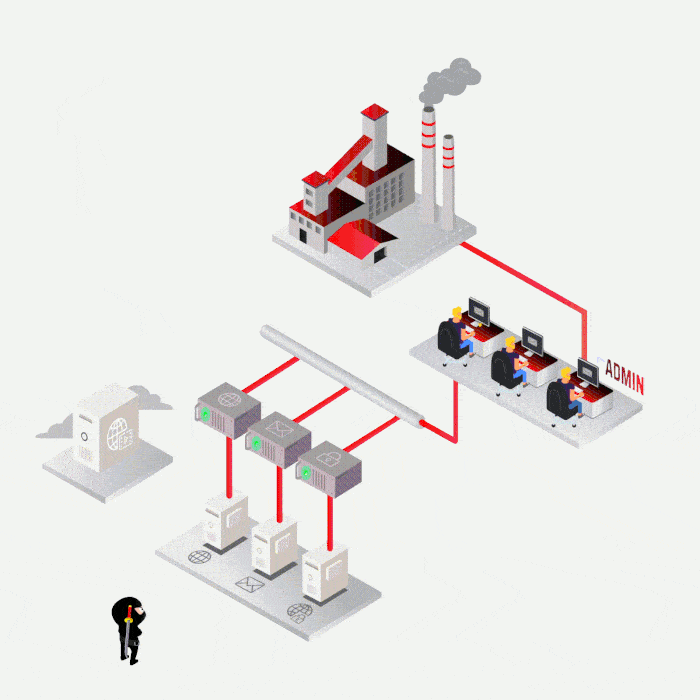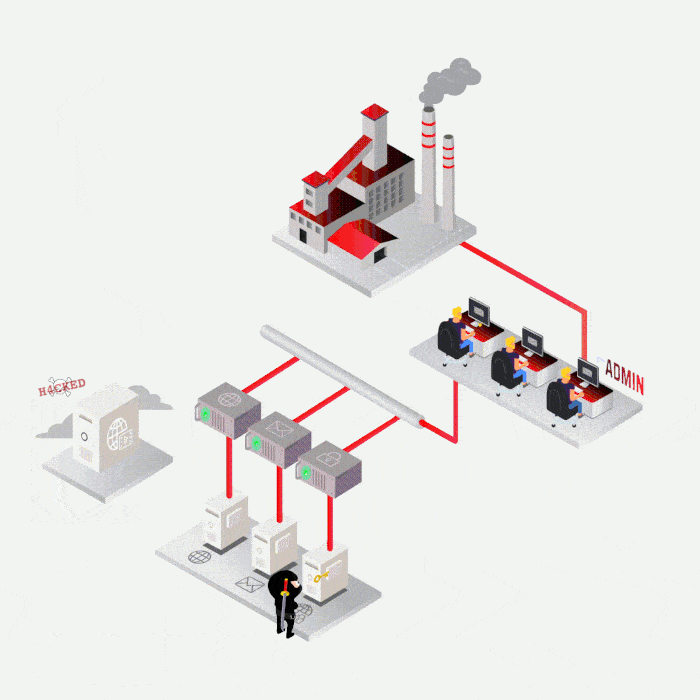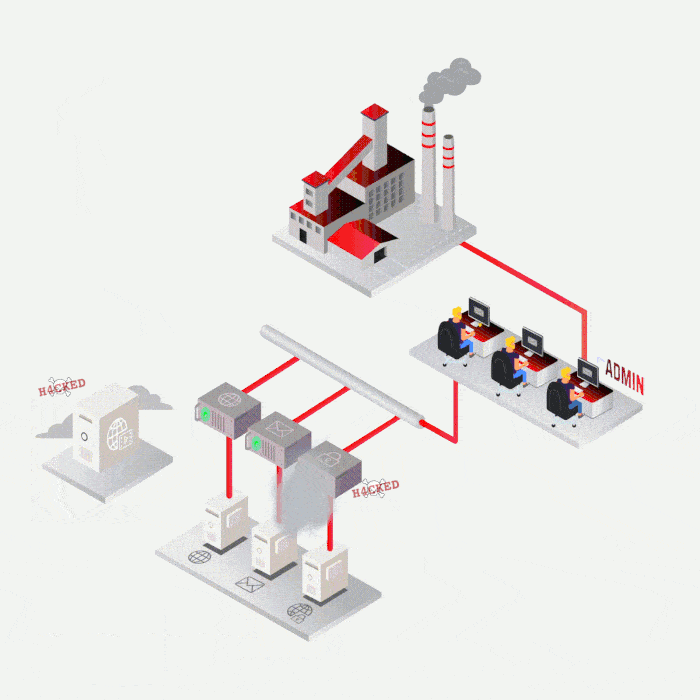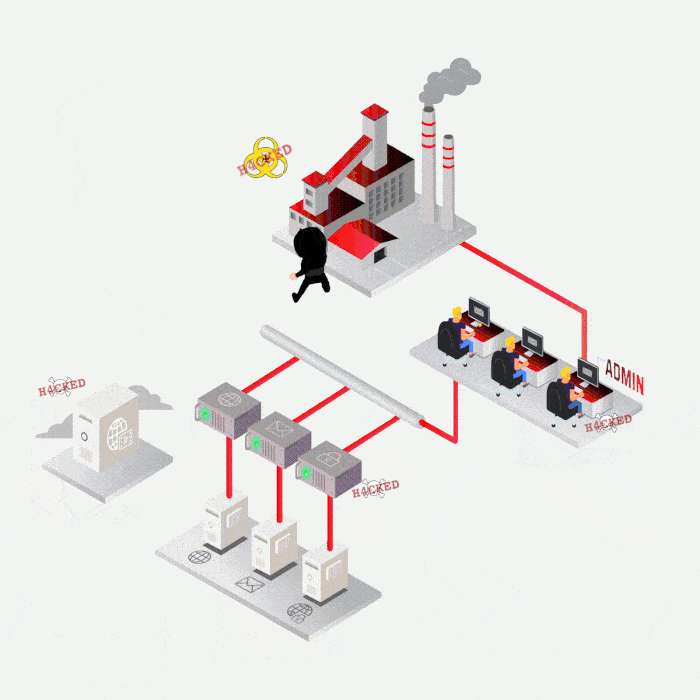
Case study
Most frequent cases
SYNACKTIV, A GUARANTEE OF TECHNICAL EXPERTISE
At Synacktiv, we make it a point of honor to ensure our clients' satisfaction. Such a result can only be achieved through state-of-the-art technical expertise and a thorough understanding of today's threats. Because we strive for constant improvement, we take part in international conferences and "Capture the Flag" competitions to perfect our knowledge and intrusion techniques.
Testimonials

Sébastien Gaïde

Marc-Antoine Lacroix

Fabien Desmoulins
Calendar
Want to train your team? Contact us to arrange a private session — either at our venue or directly at your location!
Contact: trainings@synacktiv.com, 5 boulevard Montmartre 75002 Paris

 Métro Grands Boulevards
Métro Grands Boulevards
Terms and conditions
Each session is led by two experienced trainers who will ensure optimal understanding while providing concrete feedback. All the material necessary for the realization of the practical work will be provided to the students and each will have an individual environment in order to ensure an immersive learning experience.