Reverse-engineering
Synacktiv relies on a team of reversers able to test the security of software solutions - whether obfuscated or not - without having the corresponding source code
Our versatile experts can audit consumer as well as industrial programs and operating systems, regardless of their intended media: computer, phone, networking or industrial equipment, IoT, etc.
EXAMPLES OF ENGAGEMENTS
- Blackbox analysis of a proprietary DRM solution
- Reverse-engineering of a decoding video stream kernel module, as part of a security assessment
- Exploitation of a use-after-free vulnerability allowing privilege escalation on the audited system

Tools
IDA Pro, Ghidra, Binary Ninja, jeb, BinDiff, x64Dbg, Windbg, Frida,
QEMU, LLVM, AFL, libFuzzer
QEMU, LLVM, AFL, libFuzzer
Latest articles
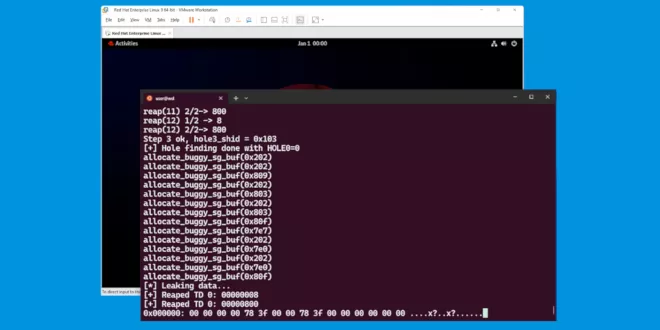
On the clock: Escaping VMware Workstation at Pwn2Own Berlin 2025
At Pwn2Own Berlin 2025, we exploited VMware Workstation by abusing a Heap-Overflow in its PVSCSI controller implementation. The vulnerable allocation landed in the LFH allocator of Windows 11, whose e
...
Breaking the BeeStation: Inside Our Pwn2Own 2025 Exploit Journey
This article documents our successful exploitation at Pwn2Own Ireland 2025 against the BeeStation Plus. We walk through the full vulnerability research process, including attack surface enumeration, c
...
Creating a "Two-Face" Rust binary on Linux
In this article we will describe a technique to easily create a "Two-Face" Rust binary on Linux: an executable file that runs a harmless program most of the time, but will run a different, hidden code
...