Kraqozorus
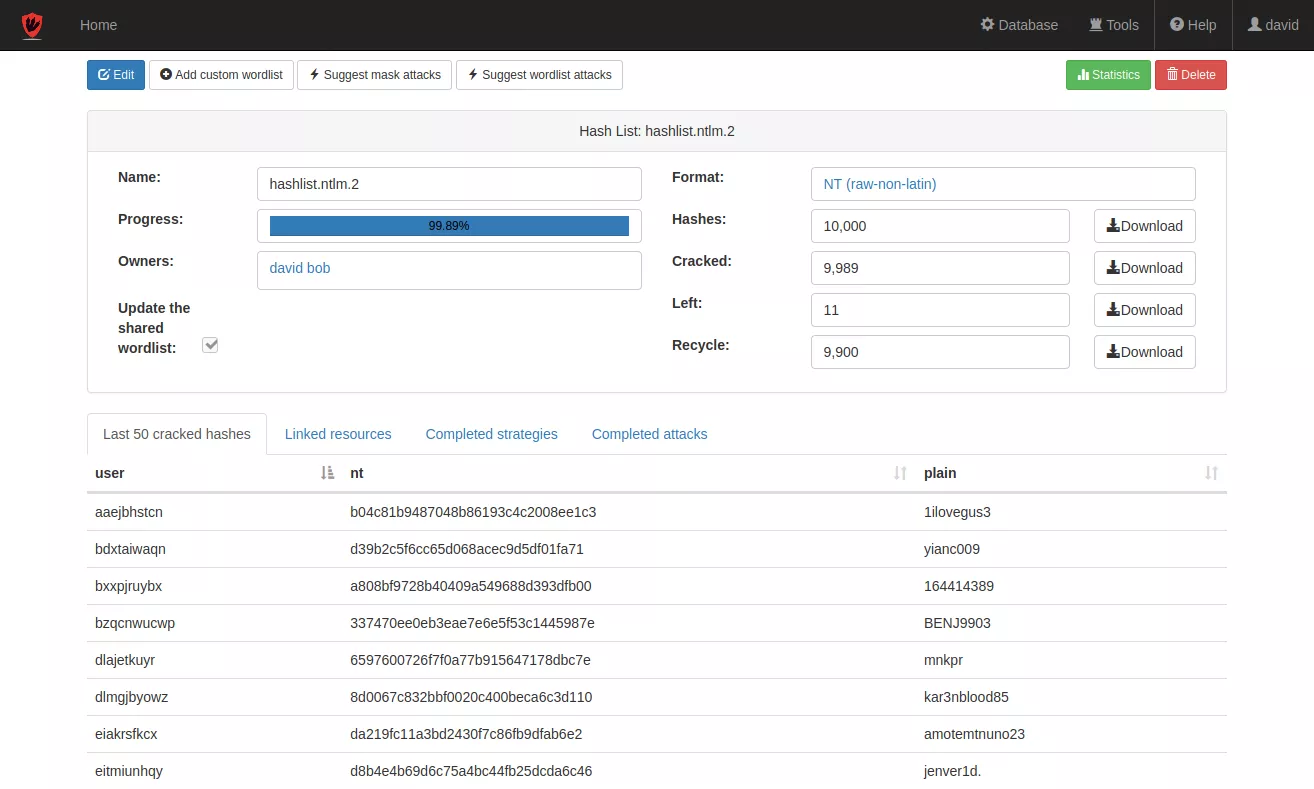
A centralized platform for password cracking.
While highly configurable and extensible, Kraqozorus is also very accessible to non technically minded users thanks to its very intuitive web user interface.
The unique concept of "cracking strategies" simplifies and accelerates the password recovery process.
Those strategies allow the chaining of complex attacks in the same way an expert would, but in a wholly automated fashion. Kraqozorus makes the best use of all CPU and GPU cores available and distributes the workload efficiently based on jobs' and users' priorities.
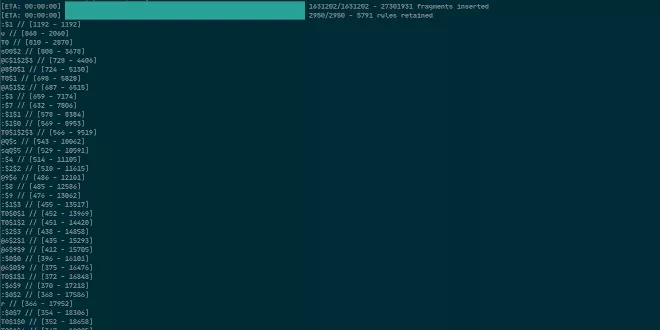
Its intelligence and optimisations allow it to crack hashes very quickly and efficiently.
Powerful
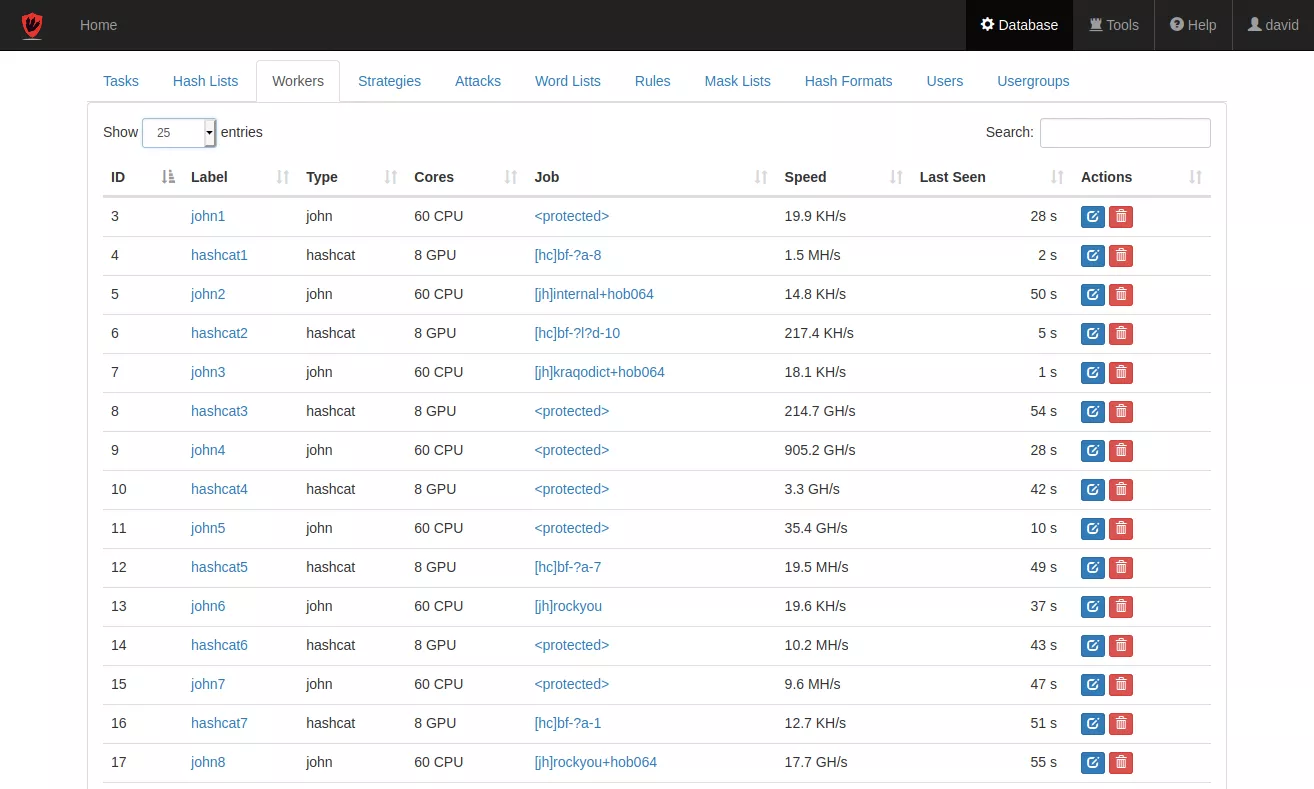
Shared computation
- Dedicated hardware configurations with multiple GPU & CPU.
- Efficient workload distribution.
- Task management allows to easily prioritize the cluster's efforts.
No performance limitations
- Up to 128 CPU and 10 GPU per server.
- Transparent horizontal scaling.
- Cluster architecture allows to connect any number of computing servers.
Collaboration
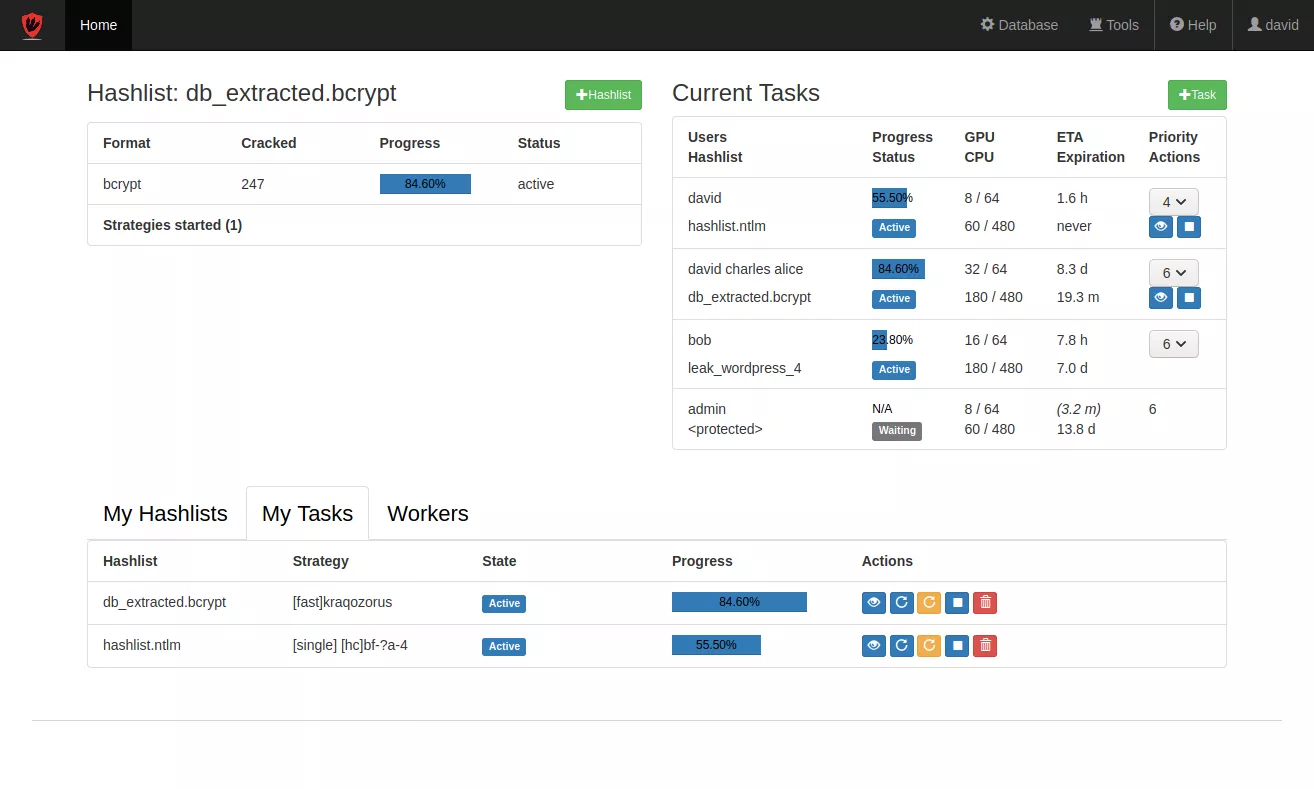
Multi user and information sharing
- User friendly interface accessible to non-technical users (drag & crack!).
- Mandatory access control lists to protect user's data.
- Email and IRC notifications. Easily extendable to other communication protocols.
Security and privacy
- User groups for isolation, resource sharing, job priorities and usage quotas.
- API that can be leveraged to automatize workflows.
Intelligence
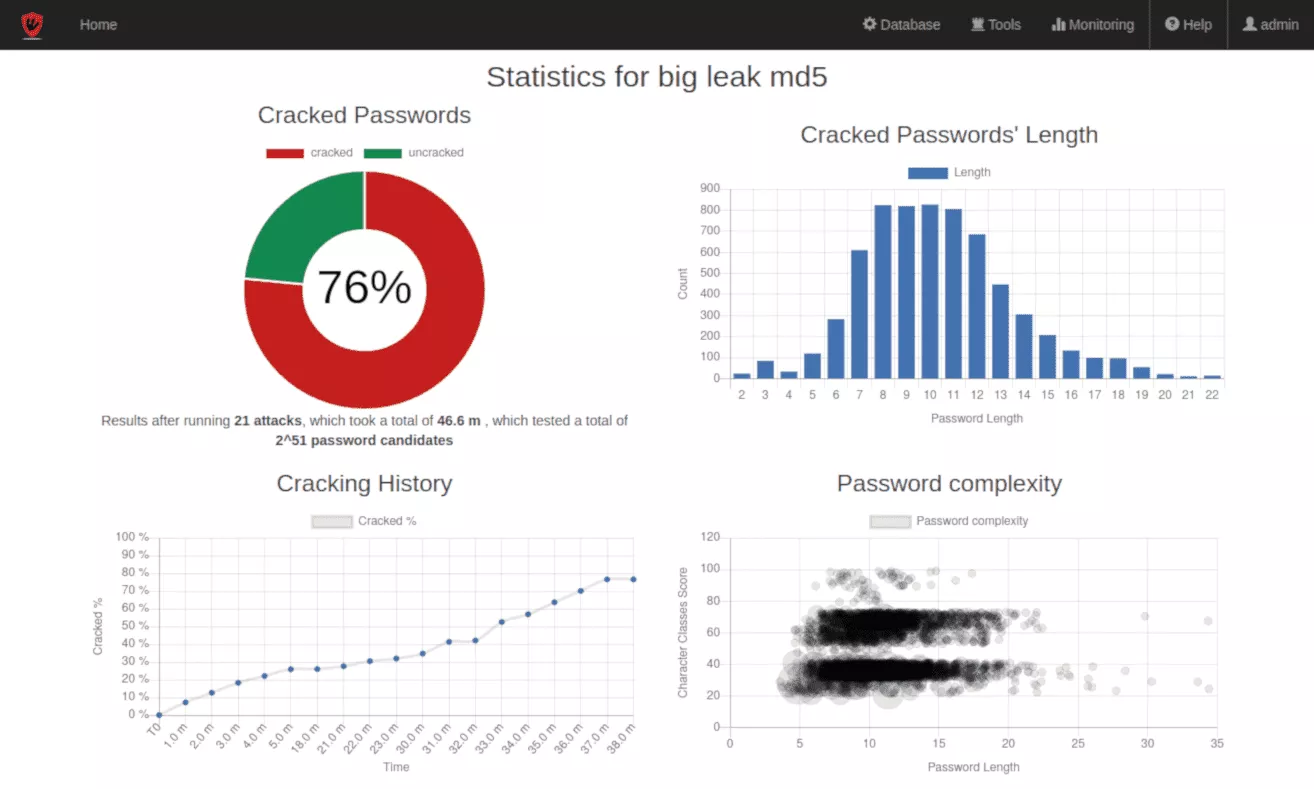
Cracking Strategies
- Unique and original concept built on Synacktiv's experience.
- Adapted attack scenarios both increase password candidates coverage while keeping minimal attacks' duration.
- Includes a password recycling mecanism to detect base-word reuses and target complex passwords.
Machine Learning
- Automatic strategy generation adapted to cluster's performances and hash formats.
- The system learns from previous tasks' results to optimize those that come after.
- Pertinent mask attack suggestions based on user preferences.
State of the art technology
Maximum attack surface
- Includes standard dictionary, mask, combinatorial and hybrid attacks.
- 19 different attack modes for both hashcat & john.
- The system comes with 116 pre-configured hash formats (NTLM, WPA, 7zip, kdbx, JWT...) and more can easily be added or personalized.
- Generation of pertinent statistics and graphics for audit reports.
Adaptability
- Built-in API to streamline workflows.
- Notification plugins to integrate in other established solutions.
- Compatible with many authentication schemes
- login / password
- SSO
- TLS client certificates
Latest articles
Writing a (toy) symbolic interpreter, and solving challenges, part 4
This is the last part of series, where we solve the challenge using our symbolic interpreter, and an external SMT solver. Huge success!
...
Unleash the dino: Time-based strategies to improve password cracking
In this article we share technical details on how Kraqozorus automatically generates password cracking strategies that improve both the number of cracked hashes and time required to run the attacks.
...
Rulesfinder, automatically create good password cracking rulesets
We wrote a new tool that automates the creation of efficient mutation rules for password crackers, such as John the Ripper or hashcat.
This posts describes the high level ideas behind this tool, al
...