Hardware investigation of wireless keyloggers
Vous souhaitez améliorer vos compétences ? Découvrez nos sessions de formation ! En savoir plus
Hardware keyloggers can be bought online for a couple of dollars and are very appreciated due to their discretion because they cannot be discovered by endpoint security software. The only condition for attackers is the usage of an external keyboard. We can assume they are used for espionage, while no public communication exists for such usage apart from a few articles123. They can be bought on many websites, even Amazon, making them commonly used in private life, for example during a divorce4. Many vendors also highlight their usage for monitoring employees. These vendors also sell other kind of recording devices, such as video (recording VGA, HDMI or DVI), RS232 and even Ethernet loggers. For all these tools, the price varies according to storage capacity and features (time keeping, Wi-Fi access...). Additionally, backdoored keyboards or small PCBs to insert in existing ones can also easily be bought online.

It is the smallest hardware keylogger available on the market, making it a professional surveillance and security tool. - https://www.keelog.com/
The parent or employer does not need to be familiar with operating a complicated software to monitor the activities of children or employees. - https://www.detective-store.com/
Targets
In this article, we will focus on the analysis of two hardware keyloggers:
- KeyDemon TimeKeeper
- Airdrive Keylogger

KeyDemon TimeKeeper
The TimeKeeper is a classic keylogger. It can be configured for a specific layout and a time can be set if the attacker knows in advance the exact time when the keylogger will be plugged. For accessing the data, a three key combination must be pressed, which will mount the keylogger as a USB drive. This combination can also be configured in the config file. The main inconvenient for an attacker is the need of two physical accesses, a first one to drop the keylogger and a second one to get it back.
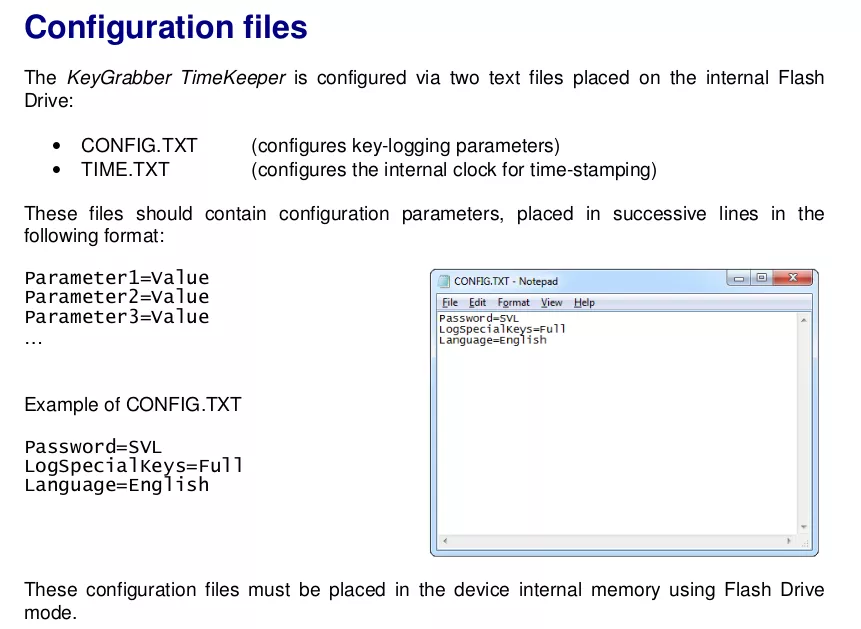
The configuration file is in the same folder as the logged keystrokes:
$ cat config.txt
Password=KBS
LogSpecialKeys=Full
DisableLogging=No
DisableLayout=No
Encryption=No
Timestamping=Yes
$ head LOG.TXT
[2016/2/23 18:24:00][Time set]
[2016/2/23 18:25:23][Pwr][Sh]Helo ld [Sh]0[Ent]
[Sh]Hello [Sh]World [Sh]1[Ent]
[Sh]Hllo [Sh]World [Sh]2[Ent]
[Sh]Hello [Sh]World [Ent]
[Sh]Hello [Sh]World [Sh]4[Ent]
[Sh]Hello [Sh]World
[2016/2/23 18:25:33] [Sh]5[Sh]Hello [Sh]World [Sh]6[Sh]Hello [Sh]Wold [Ent]
Investigating this kind of device is pretty simple. You can simply brute force all the magic combination using an Arduino/Teensy/Rubber ducky/Flipper zero.
Code for Teensy:
void setup() {}
void loop() {
delay(1000);
for (int i = 4 ; i < 30 ; i++) {
for (int j = 4 ; j < 30 ; j++) {
for (int k = 4 ; k < 30 ; k++) {
if ((i != j) and (j != k) and ( i != k)) {
Keyboard.press(i | 0xF000);
Keyboard.press(j | 0xF000);
Keyboard.press(k | 0xF000);
delay(150);
Keyboard.releaseAll();
}
}
}
}
delay(1000);
while(1) {}
}
Code for Arduino:
void setup() {
Keyboard.begin();
}
void loop() {
delay(1000);
for (int i = 97 ; i < 123 ; i++) {
for (int j = 97 ; j < 123 ; j++) {
for (int k = 97 ; k < 123 ; k++) {
Keyboard.press(char(i));
Keyboard.press(char(j));
Keyboard.press(char(k));
delay(150);
Keyboard.releaseAll();
}
}
}
delay(1000);
while(1) {}
}
Airdrive Keylogger
The Airdrive Keylogger is a keylogger with a Wi-Fi hotspot which can be used to configure it and remotely dump the captured keystrokes.
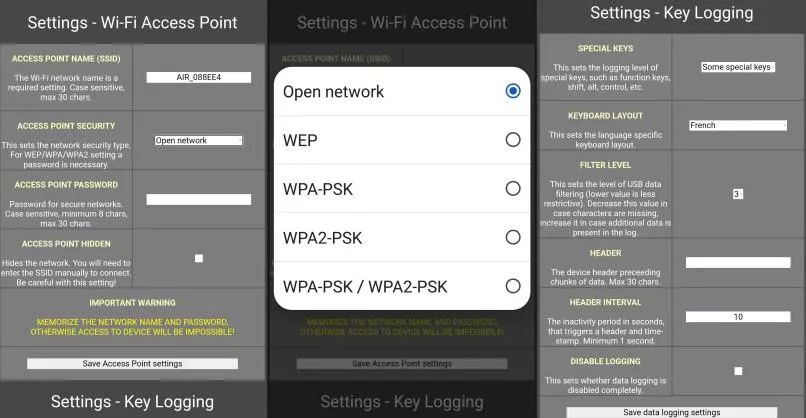

To access the device, our first attempts focused the Wi-Fi interface. By default, the keylogger is providing an access point with the AIR_XXXXXX name pattern (the SSID can be changed and/or hidden). However, because no client is connected on the device and the Wi-Fi chip is not vulnerable to the PMKID attack5, the only remaining method was to brute force the PSK online, which is pretty slow and rarely successful.
ESP8266 inside
Our approach was therefore to open the device, which revealed a simple layout with all the interesting hardware on the same side:

- A 5M160Z chip.
- An ESP8266 chip, used for the Wi-Fi interface.
- A Winbond Flash used for storage.
Flash dump
The Winbond Flash can easily be identified by reading the reference from its shield: 25Q128JVSQ. Performing a dump of such chips is common and well documented on the Internet, and an Hydrabus was used to do so6 with a clip. However, trying to read the flash will not work due to VCC being connected to the master component on the device. As we are powering the flash during the dump, the main chip is powered up and also tries to access it.
An easy solution is to unsolder the Winbond Flash and read it offline. Another way would have been to put the SoC in RESET mode in order to prevent it from accessing the flash.
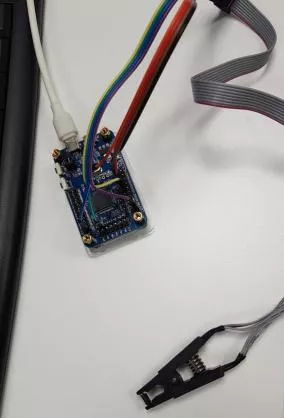
$ ./flashrom -p serprog:dev=/dev/ttyACM0 -r /tmp/dump.bin -c "W25Q128.V"
Using clock_gettime for delay loops (clk_id: 1, resolution: 1ns).
serprog: Programmer name is "Hydrabus"
Found Winbond flash chip "W25Q128.V" (16384 kB, SPI) on serprog.
Reading flash... done.
Dump analysis
The great and powerful strings command is sufficient to retrieve the SSID, the PSK and the logged keystrokes.
$ strings dump.bin | grep -C5 AIR_089658
55151322
RNJD@8
!%.
|8|9|:|;|<|=|x|y|z|{|||}|
RNJD@8
AIR_089658
azertyuiop
AIR_089658
<p>coucou[Ent]
A smarter analysis using hexdump reveals chunks with the SSID and PSK, as well as the keystrokes.
$ hexdump -C dump.bin
[...]
*
000fd0a0 ff ff ff ff ff ff ff ff ff 00 ff ff ff ff ff ff |................|
000fd0b0 0a 00 00 00 41 49 52 5f 30 38 39 36 35 38 00 00 |....AIR_089658..|
000fd0c0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
000fd0d0 00 00 00 00 61 7a 65 72 74 79 75 69 6f 70 00 00 |....azertyuiop..|
000fd0e0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
*
[...]
Interesting part, the recovered data is still available even after erasing it from the web interface. The correct way to erase the logged keystrokes would then be to first use the erase function from the web interface, then log junk keystrokes to overwrite the previous ones (this can be automated using a Teensy), and finally use the erase function again.
Next steps for the blue teams
Usage of the compromised accounts must first be investigated. In addition, fake data could also be added to the keylogger such as a honeypot account, which could help detecting future attacks. This may also help to identify the attacker during a law procedure.
Regarding the Wi-Fi device, it is also possible to monitor connections using bettercap. First, the BSSID of the target is found:
wlxa0f3c11a2f72 » wifi.recon on
wlxa0f3c11a2f72 » wifi.show
┌─────────┬───────────────────┬────────────┬────────────────┬─────┬────┬─────────┬──────┬───────┬──────────┐
│ RSSI ▴ │ BSSID │ SSID │ Encryption │ WPS │ Ch │ Clients │ Sent │ Recvd │ Seen │
├─────────┼───────────────────┼────────────┼────────────────┼─────┼────┼─────────┼──────┼───────┼──────────┤
│ -44 dBm │ 42:f5:xx:xx:xx:xx │ AIR_XXXXXX │ WPA (TKIP, PSK │ │ 1 │ │ │ │ 16:56:56 │
└─────────┴───────────────────┴────────────┴────────────────┴─────┴────┴─────────┴──────┴───────┴──────────┘
Then, this BSSID is monitored:
wlxa0f3c11a2f72 » wifi.recon.channel 1
wlxa0f3c11a2f72 » wifi.recon on
wlxa0f3c11a2f72 » wifi.recon 42:f5:yy:yy:yy:yy
When a successful connection is performed, bettercap creates a file with the captured handshake. This indicator can be used to monitor the proximity of the attacker.
wlxa0f3c11a2f72 » [16:58:43] [wifi.client.handshake] captured xx:xx:xx:xx:xx:xx -> AIR_XXXXXX (42:f5:yy:yy:yy:yy) WPA handshake (half) to /root/bettercap-wifi-handshakes.pcap
wlxa0f3c11a2f72 » [16:58:43] [wifi.client.handshake] captured xx:xx:xx:xx:xx:xx -> AIR_XXXXXX (42:f5:yy:yy:yy:yy) WPA handshake (half) to /root/bettercap-wifi-handshakes.pcap
wlxa0f3c11a2f72 » [16:58:43] [wifi.client.new] new station xx:xx:xx:xx:xx:xx (Murata Manufacturing Co., Ltd.) detected for AIR_XXXXXX (42:f5:yy:yy:yy:yy)
Conclusion
Hardware keyloggers are cheap, making them accessible to everyone. However, this low price also comes without advanced security, making their investigation simple. This article described the first steps blue teams could follow to determine the compromised data and detect further attacks from their opponents.
- 1. https://www.bleepingcomputer.com/news/security/student-expelled-for-usi…
- 2. https://cybersecuritynews.com/agarwal-hardware-key-logger/
- 3. https://www.dailymail.co.uk/news/article-3281805/Three-students-charged…
- 4. https://www.rosen.com/divorce/divorcearticles/keylogger-nc-divorce/
- 5. https://hashcat.net/forum/thread-7717.html
- 6. https://github.com/hydrabus/hydrafw/wiki/HydraFW-SPI-guide#flashrom-usa…
