SAP Financial Consolidation - Admin authentication bypass
16/06/2025 - Download
Product
SAP Financial Consolidation
Severity
Critical
Fixed Version(s)
Release version not public
Affected Version(s)
10.1 SP09 Patch 02
CVE Number
CVE-2025-30016
Authors
Description
Presentation
SAP Financial Consolidation provides enterprise-class consolidation features for statutory and management reporting to meet complex consolidation requirements, close your books quickly and accelerate the financial close process.
Issue(s)
All local accounts, including the built-in default ADMIN account can be used with a hardcoded password without knowing their actual password.
Timeline
| Date | Description |
|---|---|
| 2025.02.10 | Advisory sent to SAP |
| 2025.04.08 | Patch published |
| 2025.06.16 | Public release |
Technical details
Authentication bypass
Description
The SAP Financial Consolidation relies on dynamic libraries, one of them implementing security functions (CtSecurity.dll). A file containing debug symbols is also present on the installation folder (CtSecurity.pdb).
The analysis of this DLL using the symbols allows identifying key functions related to authentication. The CCtAPCOMAuthenticationProvider::Authenticate function starts with a string comparison.
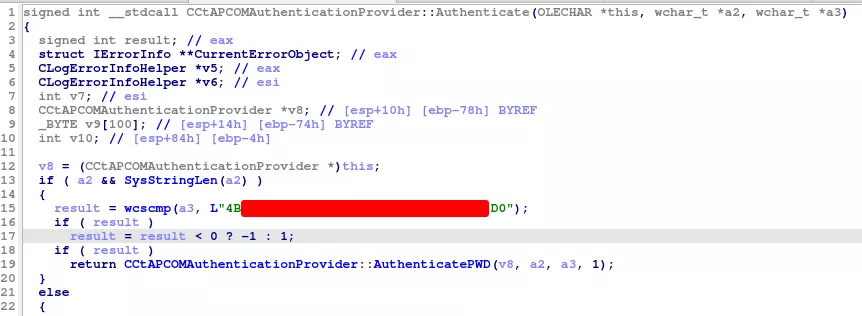
This hardcoded string can be used as a password when authenticating with the ADMIN user, and all local accounts, allowing to obtain access with the web application and the thick client.
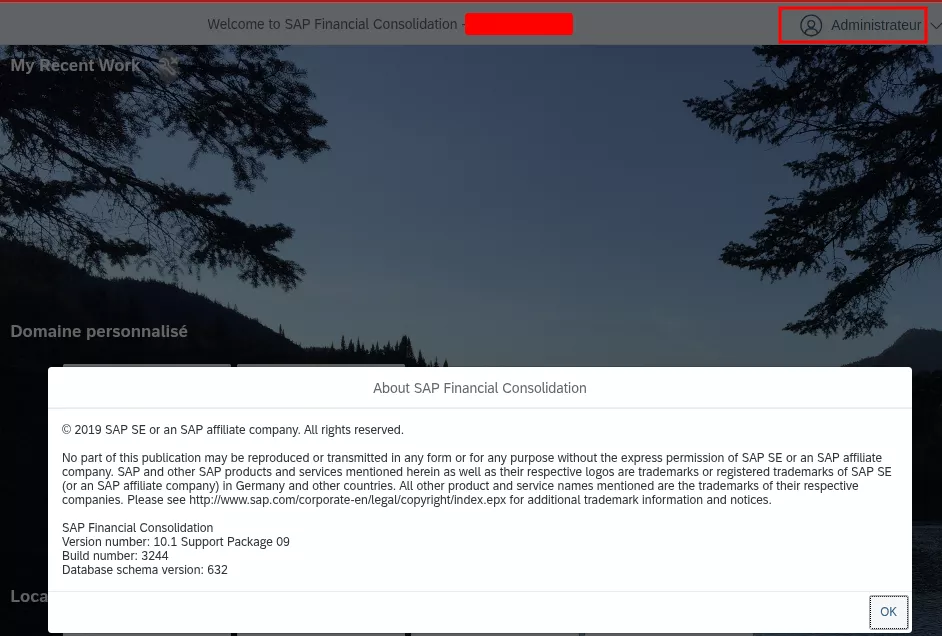
Impact
The vulnerability allows bypassing authentication for all local accounts, including the built-in ADMIN account which has the highest privileges on the application. All data of the application can be retrieved. Moreover, natively, tasks can be executed while specifying arbitrary programs and arguments, which can lead to the compromise of the underlying system.
